By Dr.Debarati Halder, LL.B., M.L., Ph.D(Law) (NLSIU)

The modern human society is overly dependent on the internet now. Artificial intelligence and Internet of things (IOT) have made it possible for machines to work and speak for humans. In other words, human minds are now ‘colonized’ by machines which compel most human beings to think, act and text what they (the machines) want the later to do. While this statement may be considered as ‘dramatic’. The fact is, the machines are controlled by human intelligence. This human intelligence (which controls the machines) is developed by few skilled people who may have developed the software, the hardware and may have done the entire designing of machines for the benefit of human society. This human intelligence is the main factor which empowers the machines to control the thought process, activities and execution of the thought process of many other human beings.
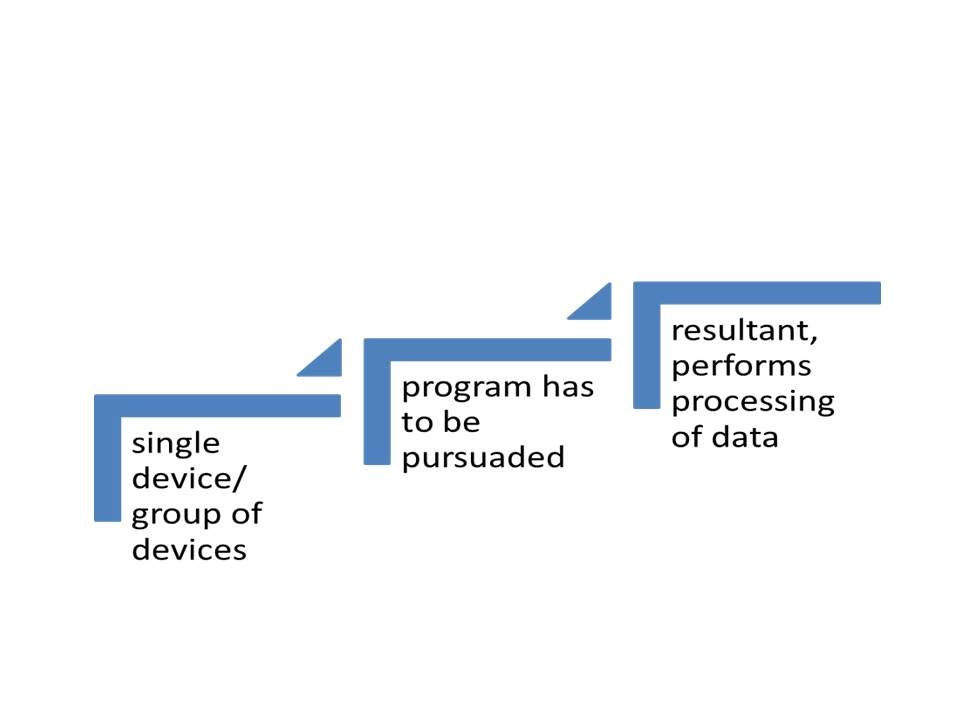
Let us understand this process through the following diagram :

A fine example of this could be using automatic washing machines. Almost every households have washing machines and many of them are automatic. This auto mechanism is the first box : humans make software and user-friendly hardware understanding the needs of fellow human beings. Next , the machines get adjusted to human needs. No, it’s not about befriending humans; it’s about how the machine decides how much clothes should be washed /dried on a daily /weekly basis, what should be the water temperature and how best that temperature may suite the clothes. Next, humans get dependent on the machine, its artificial intelligence and its ability. The manual work time that should have been done by the humans, is now taken over by the machine. The humans now can use this time for more positive (and in several cases negative too) productive works. The psychology of human beings then becomes completely connected with the machines and dependent on the machines. At one point of time, when the machine stops working or does not perform according to the expected performance level of humans, the later becomes angry, irritated, annoyed. What we see here is the connection between human psychology and artificial intelligence. This is a unique connection between physical space and mental space, which is bridged by something called cyber space. Let us understand the typology of space here:

Physical space is that space for which laws may be made for governing behaviors, contracts, marriages, succession, criminal and civil liabilities etc. Traditionally laws are made for controlling those incidences which can be felt physically, financially and to a certain extent psychologically. Consider Penal laws meant for governing criminal activities like causing grievous physical harm. Law is made to address pre execution plan, execution of the plan and post execution impact on the body, mind and society as a whole. It is for this reason that we get to see the application of law meant for abetment, motive, means rea, commission of offence, compensation, punishment of the offender and also rehabilitation of the offender as well as the victim.
Mental space on the other hand, is a logical and formal abstract space where ideas may generate. Laws may be created for governing outer behavior of individuals. But mental space may not be governed by any law. It has to be disciplined to think create action plans as per the positive societal norms. A good example of law versus mental space can be, a plan to commit a theft is made in the mind. Until and unless this is executed and committed in the physical space, it can not be prosecuted or laws can not be used to regulate that particular act. This means that planning or thinking something in mind and doing the same on physical space are two different things. Unless both are connected by plan and consequent action and execution of the plan, laws may not be applied.
Cyber space on the other hand, is a virtual space where machines are made to work at the command given by humans. Laws are necessary to govern this space because it executes several plans or motives, makes contracts and creates criminalities and civil liabilities too. however, there is a common overlapping of the concepts of cyber space and internet.
On 1st April,2019, Gmail celebrated its 15th birthday. This free email service by Google rapidly became popular across the globe and threw a tough competition to other email services including Hotmail, Yahoo mail, AOL mail etc. These are also known as web mail services. They are termed as Web mail services because unlike postal mail services, these web mail services connect people through cyber space, which, to many is popularly known as Worldwideweb.
But technically speaking, the concept of cyber space evolved much more earlier than the concept of Worldwideweb. The abstract concept of “Cyber space” was created first by a novelist and science fiction writer William Gibson in his novel “Neuromancer”. He described the cyber space as ““A graphic representation of data abstracted from banks of every computer in the human system. Unthinkable complexity. Lines of light ranged in the nonspace of the mind, clusters and constellations of data. Like city lights, receding.”[1]
The term cyberspace is actually derived from the term cybernetics (which comes from the Greek term kybernētikḗ [2]) which was coined by Norbert Weiner in 1948. Weiner explained it as “scientific study of control and communication of animal and machine”. [3]
As one can see, the description of cyber space by Gibson not only threw light on the complexities of computer technologies, but also emphasized on involvement of human mind in operating on this space. In 1989 Tim Bernes Lee invented WorldWideWeb, which is an information space. This made the documents and other web resources easily available on the web space.

But this does not mean that WorldWideWeb or cyber space is only machine oriented. As Gibson emphasized, cyber space (and later WorldWideWeb) is necessarily controlled by human beings. Cyber Space has been used positively as well as negatively to create documents, interconnect military departments with universities for security research purposes, for networking, creating and providing huge data base for several types of information. At the same time, cyber space is also used for several criminalities, for plotting terror, for carrying out terror activities and for executing criminal activities targeting governments, corporate houses and individuals . with the emergence of internet, new information and digital communication technologies cyber space has now become the most chosen space for carrying out criminalities against individuals including women and children.
Lawrence Lessig, a fine academician and a Harvard professor addressed cyber space from the perspective of governing cyber space. According to him, the concept of cyber space can be explained on the basis of the followings[1]:
- Cyber space is a livable place.
- It has Possibility of actions
- It has its own Time organization mechanism
- It has Spatial organization
- It has distinctive four pillars of cyber space (law, norms, market, constraint)
- Cyber space is regulable.
Jaishankar Karuppannan, the Father of Cyber Criminology also added one more basic feature of cyber space, which is connected with human psychology; he said people behave differently when they move from one space to another and this ‘space’ is none other than the cyber space.[2]
The UK Cyber Security Strategy Protecting and promoting the UK in a digital world however defined the concept of cyber space from cyber security aspect.[3] According them,
- Cyberspace is an interactive domain made up of digital networks that is used to store, modify and communicate information.
- It includes the internet, but also the other information systems that support our businesses, infrastructure and services. Digital networks already underpin the supply of electricity and water to our homes, help organise the delivery of food and other goods to shops, and act as an essential tool for businesses across the UK.
- And their reach is increasing as we connect our TVs, games consoles, and even domestic appliances
According to National Military Strategy for Cyberspace Operations, a classified document, the Joint Chiefs of Staff, US, 2006, “Cyber space is a domain characterized by the use of electronics and the electromagnetic spectrum to store, modifies and exchange data via networked systems and associated physical infrastructures.”[4]
According to National Cyber Security Policy, India , 2013, Cyberspace is a complex environment consisting of interactions between people, software and services, supported by worldwide distribution of information and communication technology (ICT) devices and networks.[5]
The latest definition of cyber space could be found in the definition developed by Marco Mayer, Luigi Martino, Pablo Mazurier and Gergana Tzvetkova in their 2014 paper on how to define cyber space .[6] Their definition runs as follows:
“Cyberspace is a global and dynamic domain (subject to constant change) characterized by the combined use of electrons and the electromagnetic spectrum, whose purpose is to create, store, modify, exchange, share, and extract, use, eliminate information and disrupt physical resources. Cyberspace includes:
a) Physical infrastructures and telecommunications devices that allow for the connection of technological and communication system networks, understood in the broadest sense (SCADA devices, smartphones/tablets, computers, servers, etc.);
b) Computer systems (see point a) and the related (sometimes embedded) software that guarantee the domain’s basic operational functioning and connectivity;
c) Networks between computer systems;
d) Networks of networks that connect computer systems (the distinction between networks and networks of networks is mainly organizational);
e) The access nodes of users and intermediaries routing nodes;
f) Constituent data (or resident data). Often, in common parlance (and sometimes in commercial language), networks of networks are called the Internet (with a lowercase i), while networks between computers are called intranet. Internet (with a capital I, in journalistic language sometimes called the Net) can be considered a part of the system a).
A distinctive and constitutive feature of cyberspace is that no central entity exercises control over all the networks that make up this new domain.”
All these definitions however skirt around the concept of cyber space as developed by Lessig.
Hence, cyber space may be explained as below:

Cyber space therefore is a holistic concept of abstract space which is inclusive of computer devices that are enabled to communicate with other computers, computer networks, storage spaces that may be enabled to import and export data , communication platforms, memory and memory chips etc. Cyber space necessarily includes infrastructure, information super highway, webpages etc which facilitates information and data exchange as well.
[1] Lessig Lawrence. The Laws of cyber space. https://cyber.harvard.edu/works/lessig/laws_cyberspace.pdf. 1998
[2] Jaishankar Karuppannan. Space transition theory. “Crimes of the Internet” edited by Frank Schmalleger & Michael Pittaro, published by Prentice Hall (2008: 283-301).
[3] See https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/60961/uk-cyber-security-strategy-final.pdf
[4] https://www.hsdl.org/?view&did=35693
[5] Retrieved from http://datia.nic.in/doc/cyber.pdf
[6] Definition by Marco Mayer, Luigi Martino, Pablo Mazurier and Gergana Tzvetkova, Draft Pisa, 19 May 2014 https://www.academia.edu/7096442/How_would_you_define_Cyberspace